One common misconception is that the hardware slows down itself, which impacts your PC’s efficiency. You can then select the items under Registry Clean you want CCleaner to scan . Using these simple steps and this best free registry cleaner, I hope you have learned how to clean Windows registry. Do share your feedback and suggestions in the comments section below.
Recently, I had to recover some data from another computer which had crashed and the only thing I had left was its hard drive. The data retrieved from the registry was sufficient to exact more search warrants which led to the arrest of 22 persons and the retrieval of illegally bought goods worth more than $100,000. Subsequently, there is a two-byte value that reveals the node type.
Major Criteria Of Dll Errors Explained
https://windll.com/dll/microsoft-corporation/msvcr100
Registry files are system protected and can not be accessed by any user unless administration access is provided. Registry Repair works in Windows 10, 8, 7, Vista, XP, Server 2003, and older Windows operating systems like Windows 2000, NT, ME and 98. However, the tool is not supported after Windows 8.1. If you want to use a text editor other than your default, right-click the file and then click the “Open With” command. Right-click any REG file and then click the “Edit” command to open the file in your default text editor.
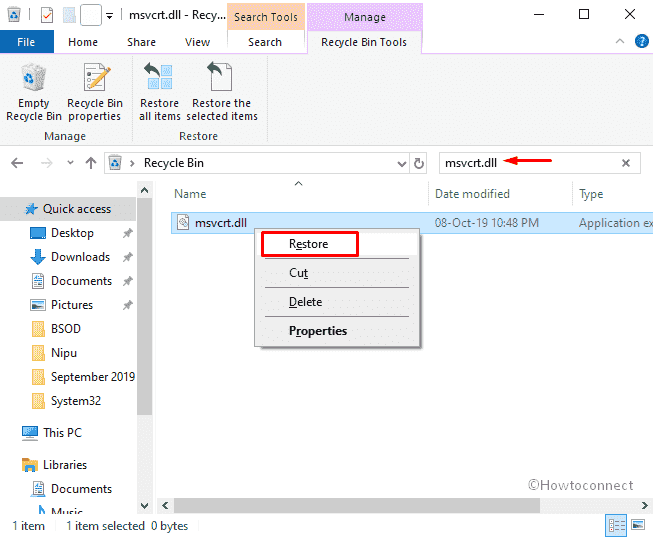
From changing the Windows design to unlocking hidden features, there are tweaks for everything. To help you improve your Windows 10 experience, here are a bunch of Windows 10 registry hacks worth trying.
Exploring Immediate Methods Of Dll Errors
With the tool, you can also backup and restore registry files. I side with Leo; I am a windows software developer, I also develop for Mac OS X and Linux. I’ve worked in the IT industry for 20 years, spent some time over at Norton removing thousands of threats of all sorts. I have several systems at home, some Windows, some Macs and a few Linux systems used by myself, my wife and 5 kids. The only systems that get issues are the Windows boxen; YMMV, but that is what is happening over here. I mean, even installing Java on Windows installs a toolbar, by default, none of that on Mac OS X or Linux.
- One nice touch is the ability to pause and continue its work anytime.
- Changing settings will only delay them but cannot stop them, especially for Windows Home users.
- One possibility in that regard might be to set it to noon if it’s common that you leave for a lunch break.
Carvey mentions in his article The Windows Registry as a Forensic Resource, an important consideration to keep in mind regarding USB device IDs. Particularly, those that have an ‘&’ symbol for the second character of the device ID. In reference to Figure 6, the Device ID that is pointed out has a serial number. However, if the ‘0’ was an ‘&’ that would indicate to an examiner that the device doesn’t have a designative serial number.
Speedy Programs For Dll Around The Usa
Each subkey maintains a list of system objects such as program, shortcut, and control panel applets that a user has accessed. The GUID subkey beginning with “5E6” corresponds to IE toolbar, while subkey starting with “750” pertains to Active Desktop . However, registry values under these subkeys are weakly encrypted using “ROT-13” algorithm which basically substitutes a character with another character 13 position away from it in the ASCII table . Even though each registry value is not associated with specific time and date the event occurred, it could imply suspect has accessed certain file or object. For instance, the existence of an attack tool’s filename on the entries could indicate suspect is trying to execute the malicious tool.